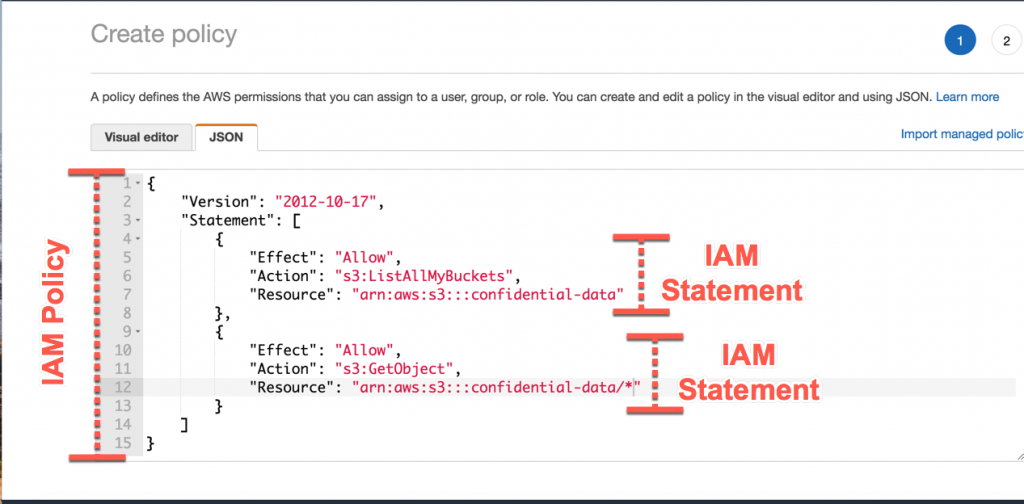
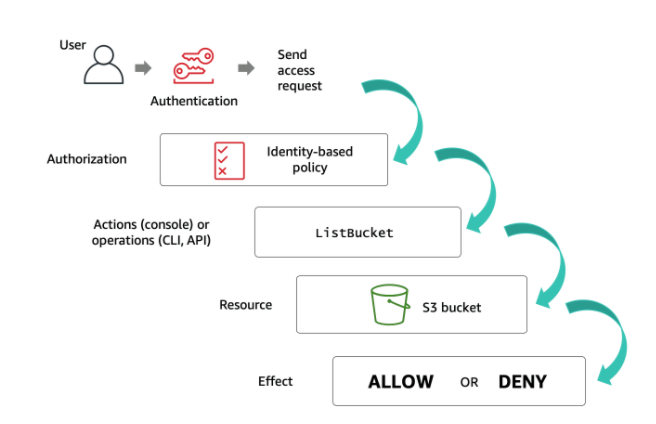
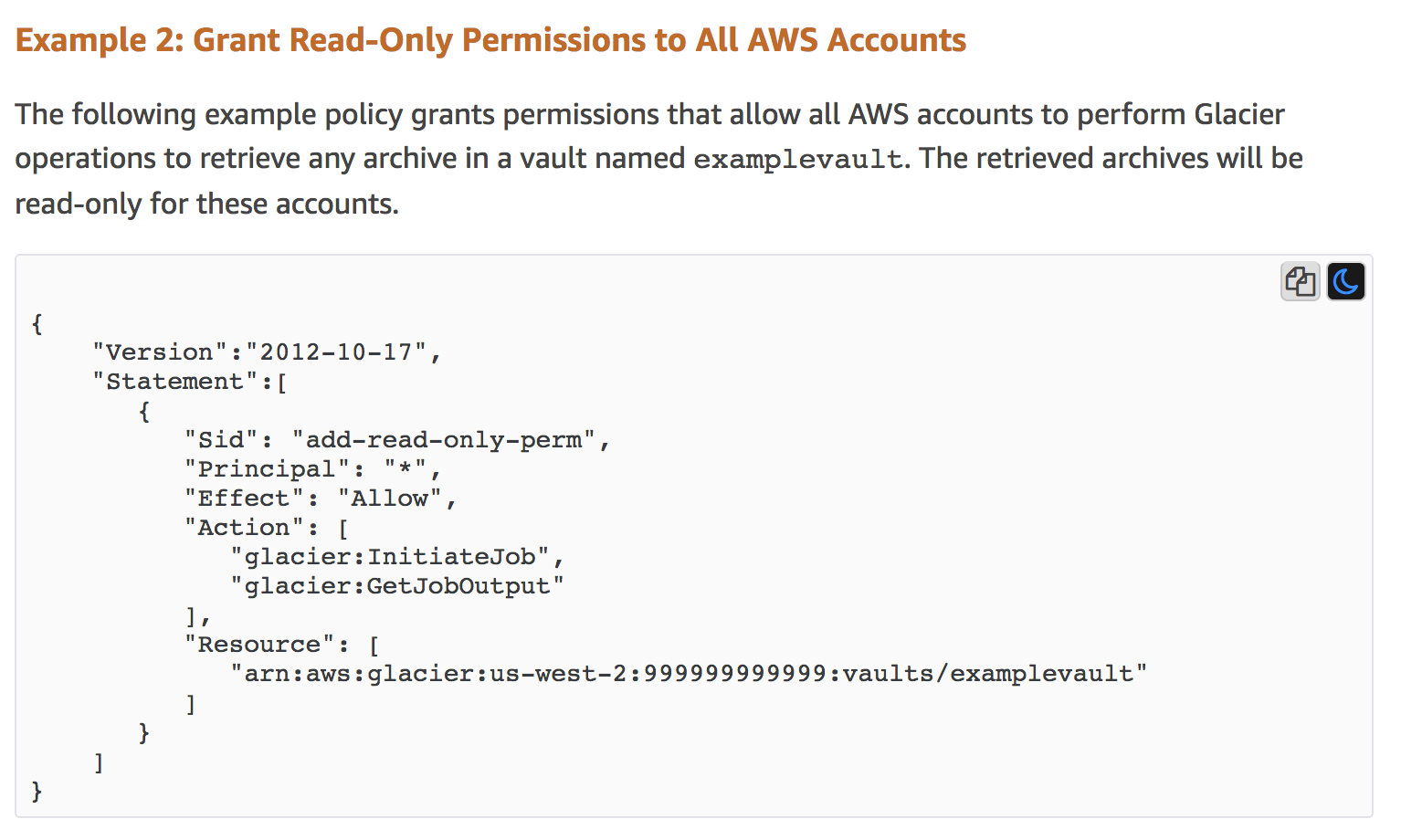
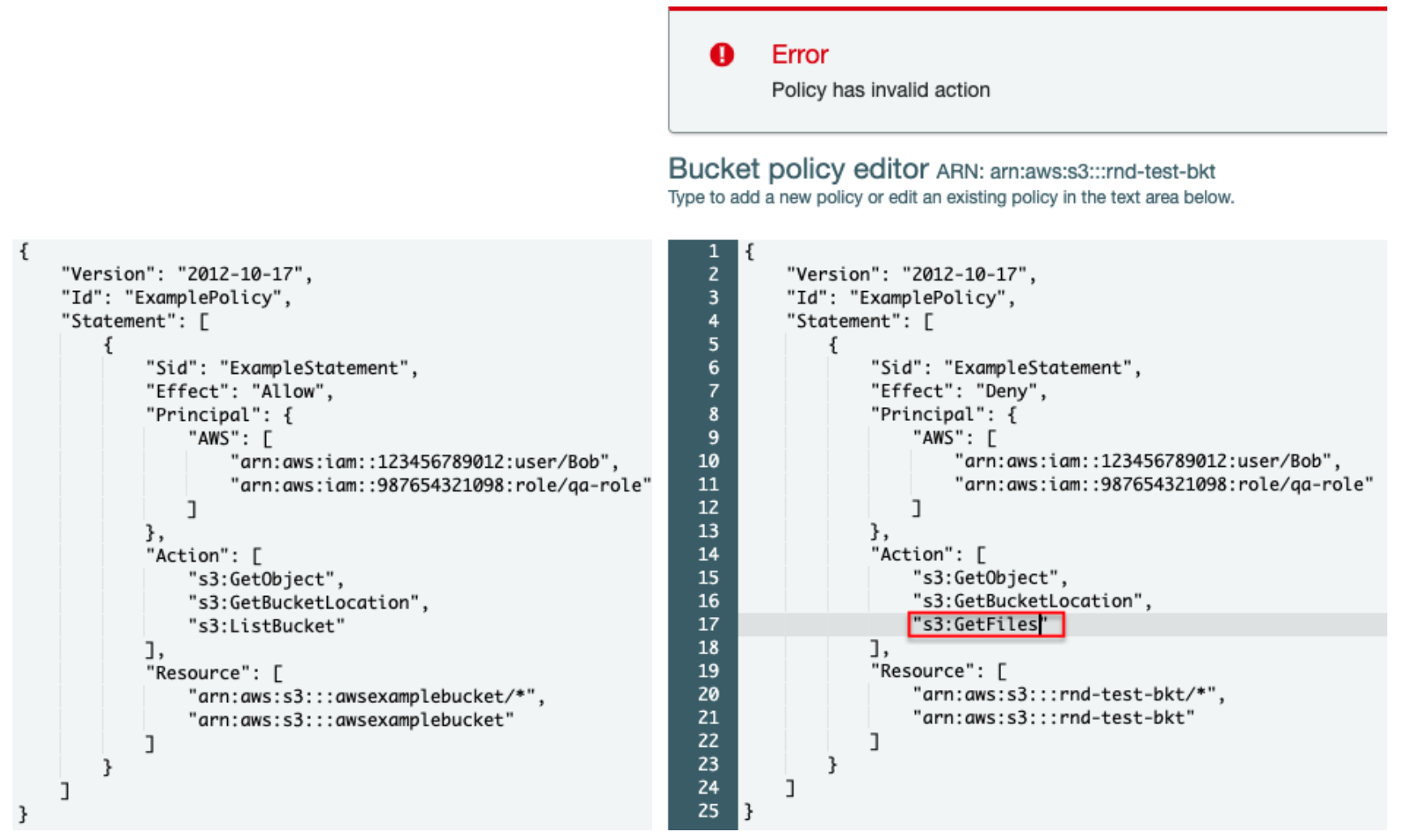
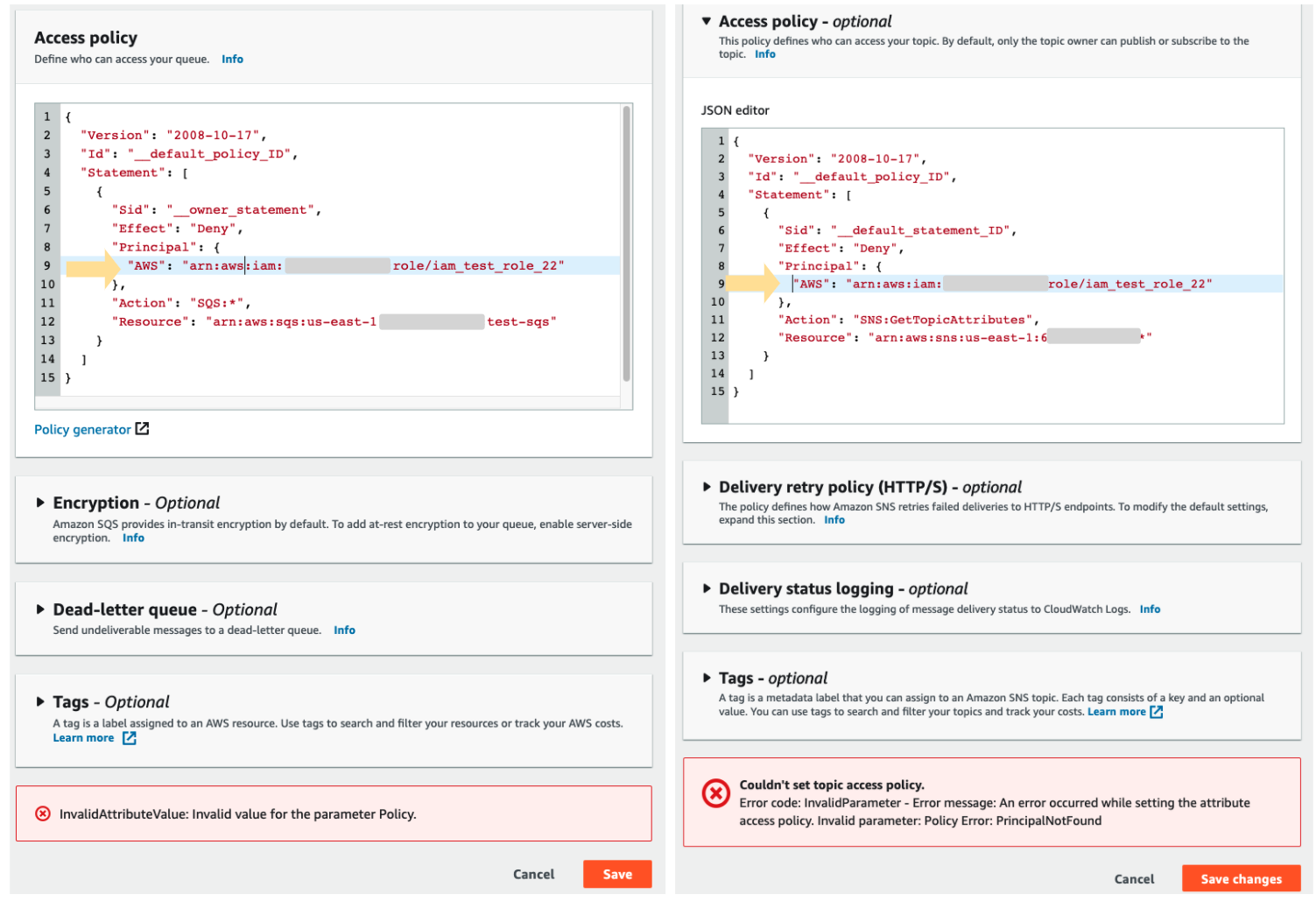
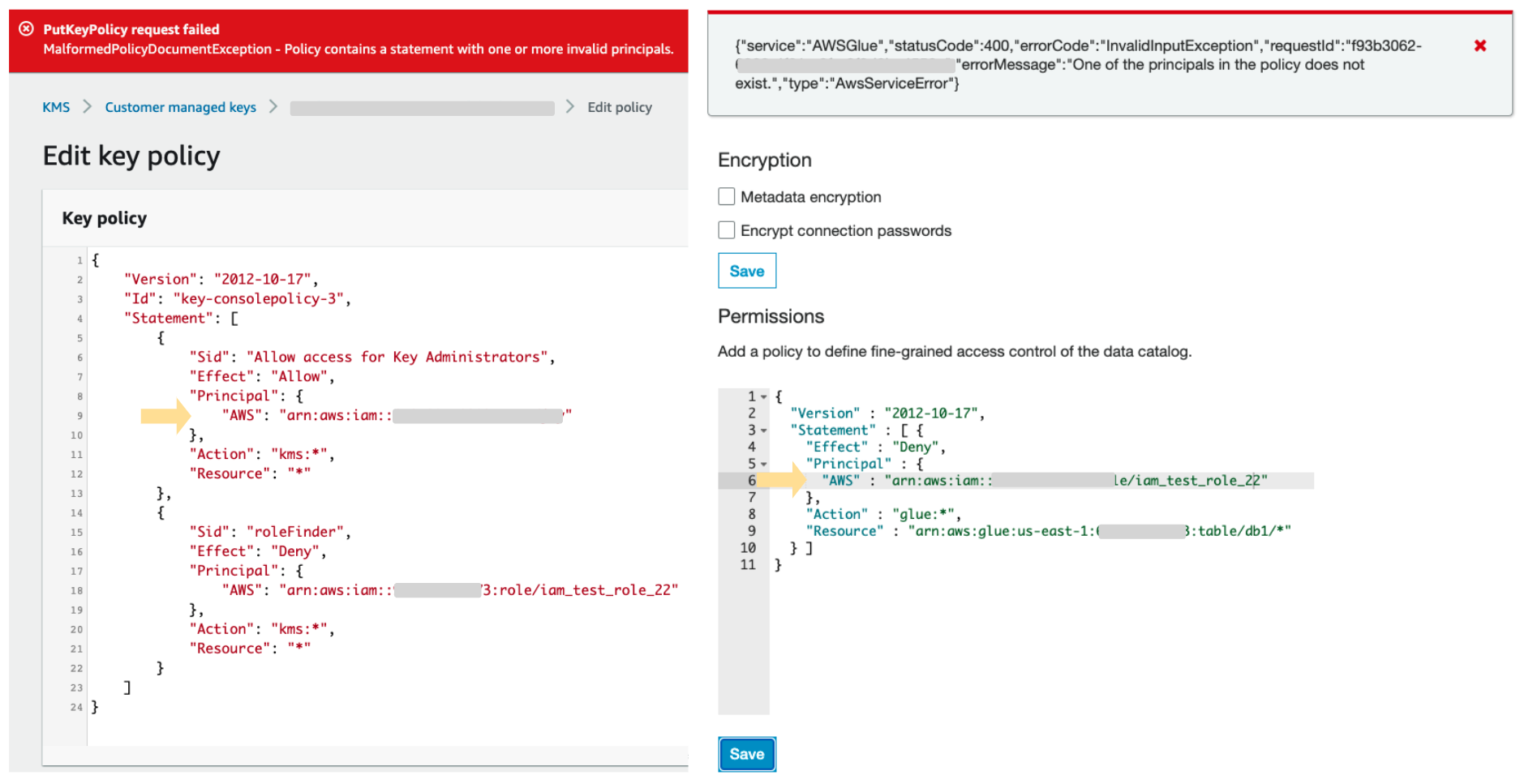
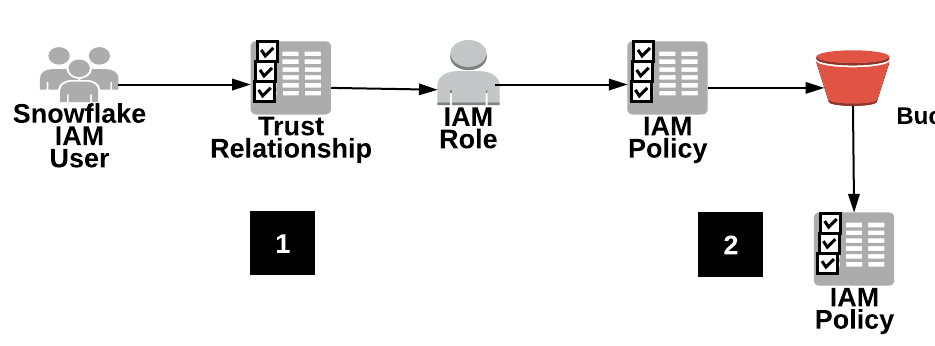
How to use resource-based policies in the AWS Secrets Manager console to securely access secrets across AWS accounts | AWS Security Blog

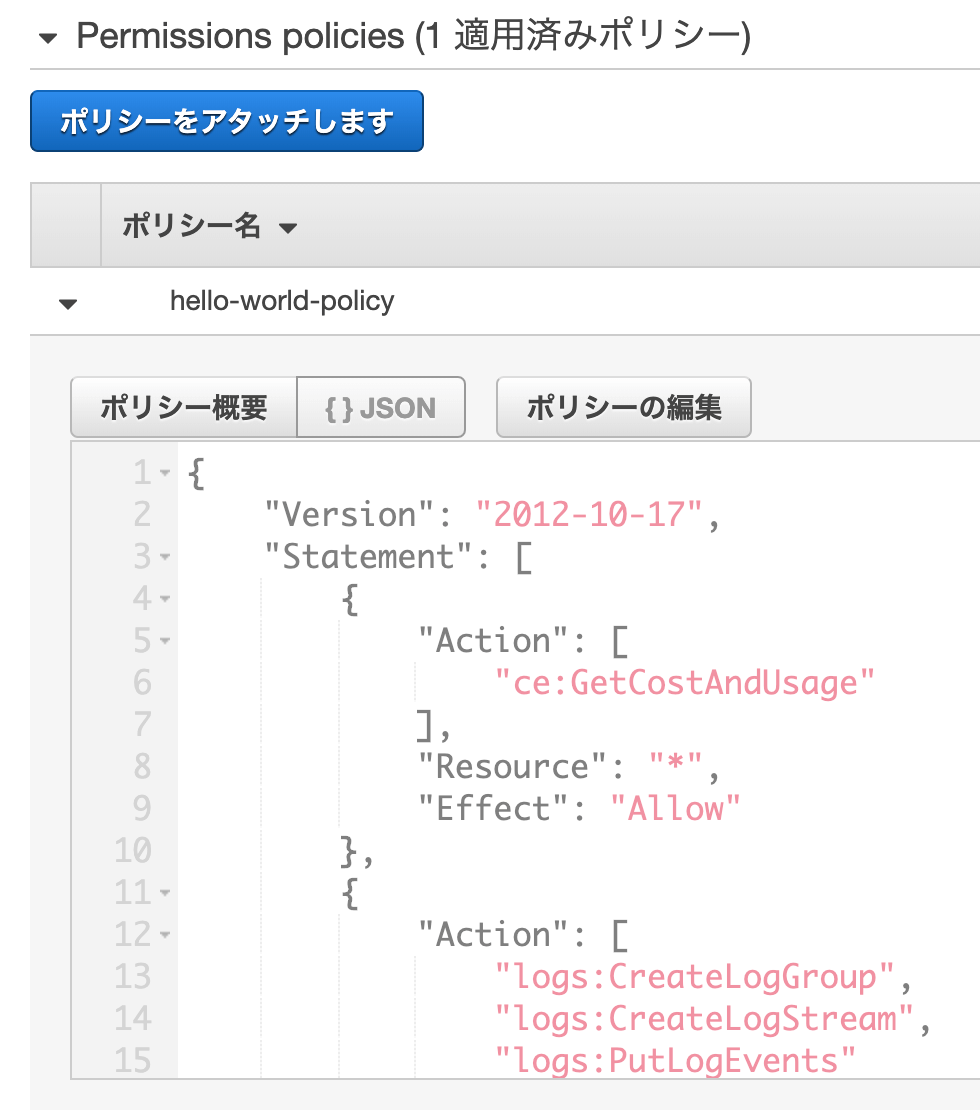
How to Create an AWS IAM Policy to Grant AWS Lambda Access to an Amazon DynamoDB Table | AWS Security Blog
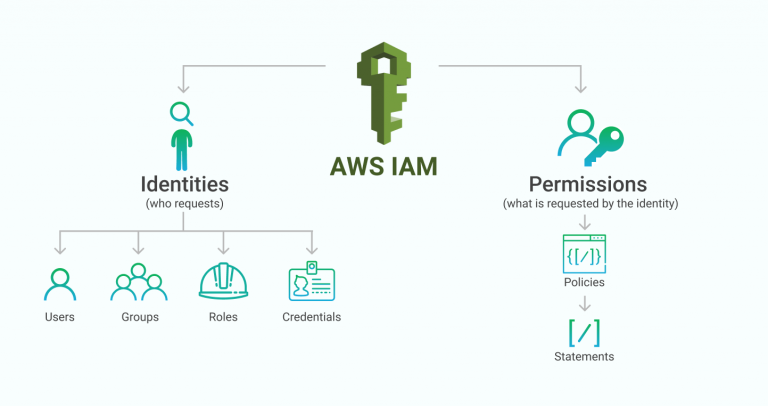
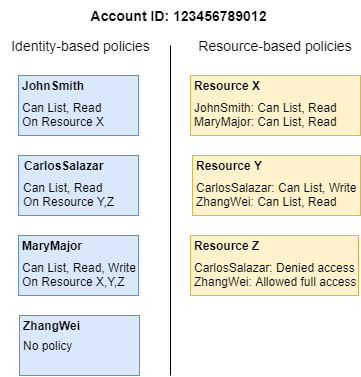
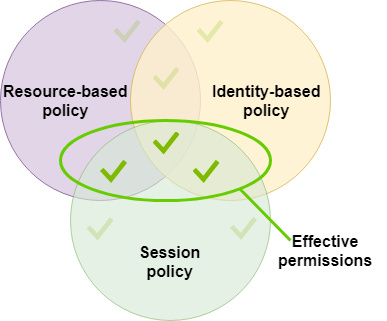
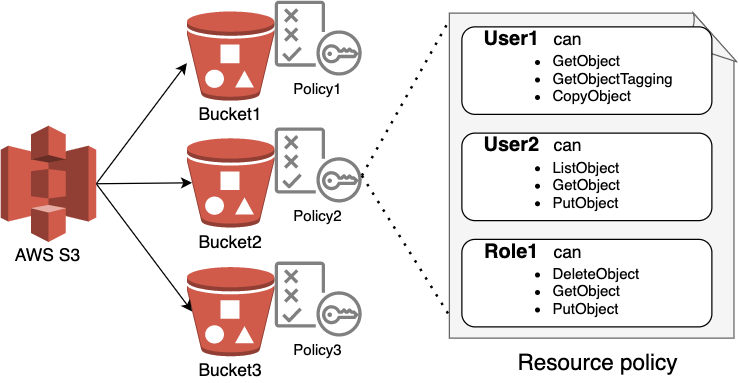
AWS IAM Primer. The 20% of IAM that you need 80% of the… | by George Lutz | Trimble MAPS Engineering Blog | Medium
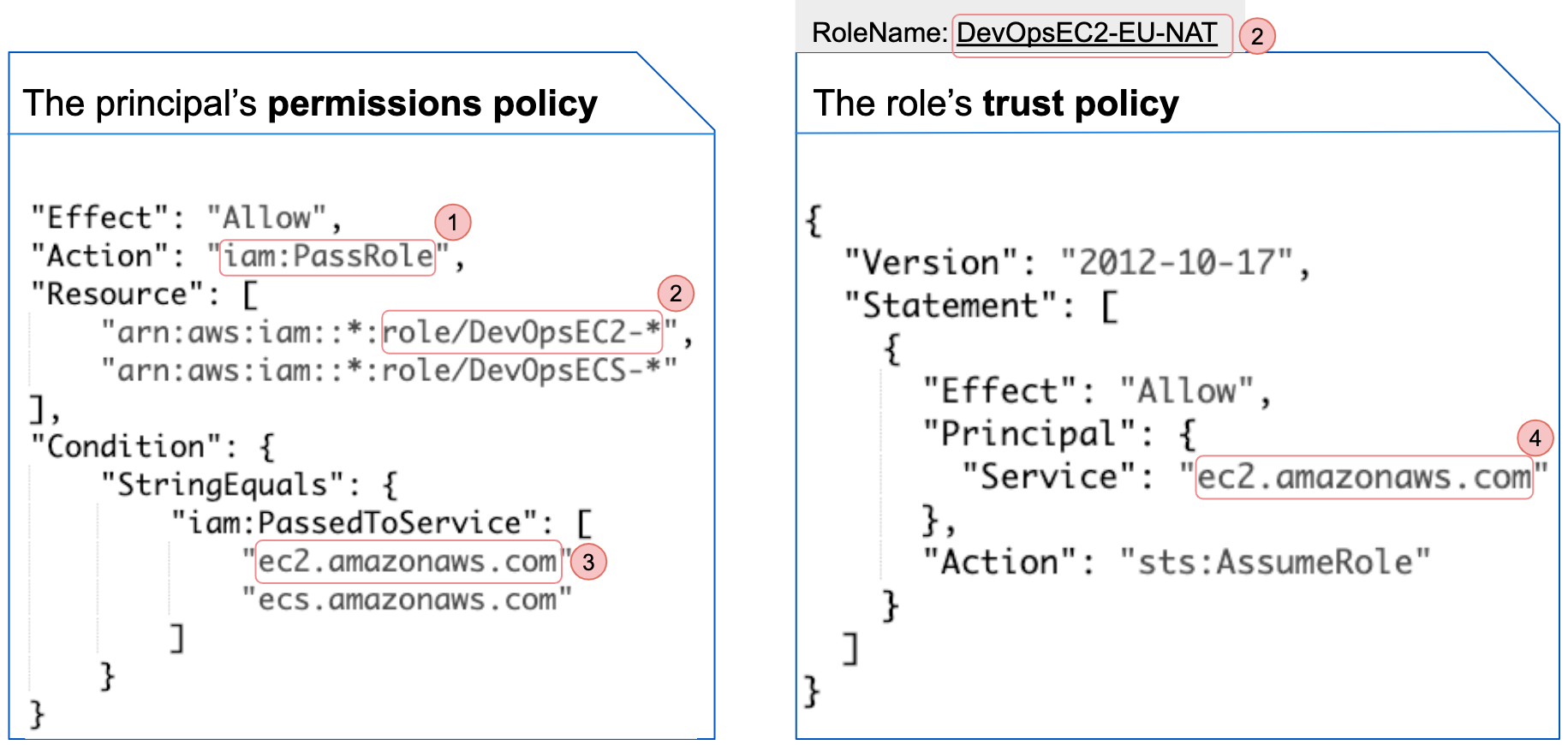
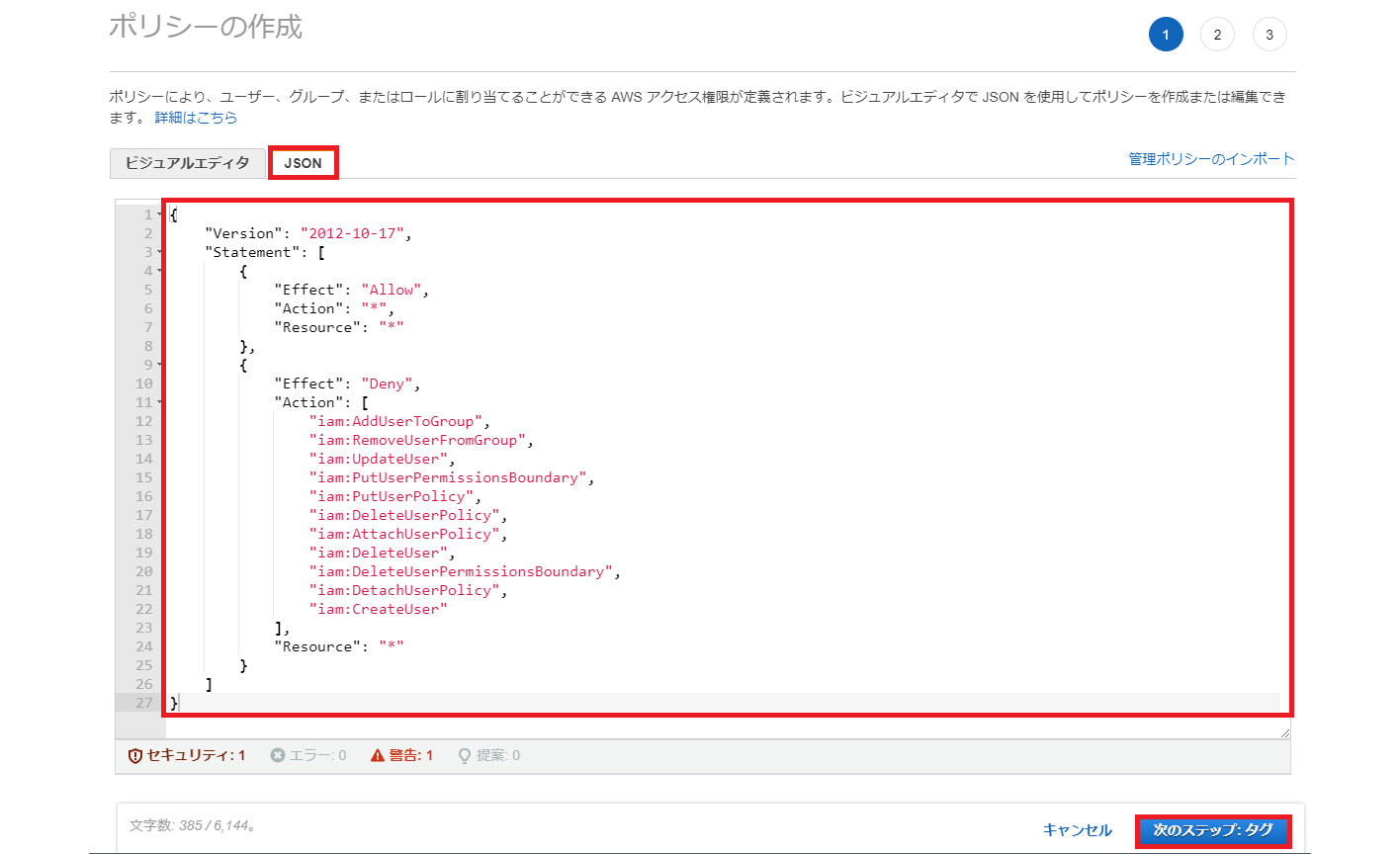
Unit 42 Cloud Threat Report: Misconfigured IAM Roles Lead to Thousands of Compromised Cloud Workloads